How to be best prepared for an interview on UNIX
You may be preparing for a UNIX Interview. If you are then you ought to be set up for the meeting with the objective that you can rouse the examiner most. The primary concern that you need to do is to be set up with some unix interview questions. There are some extraordinary things too that you ought to be set up with before you arrange yourself in the hot seat anyone would want to be. By examining the request you will have the ability to appreciate what nature of request you can be asked and what may be the correct answer if you are asked such a question. There are diverse plans in like manner that you need to make before you go for a meeting. You need to mastermind the travel unpretentious components of yours suitably. The travel should be wanted to the point that you don’t be late for the meeting. It is perfect to accomplish the scene of the meeting to some degree in front of a timetable than to be late. The accompanying thing is not to be scared at any condition. You may not make certain about a question. If it so happens then it is required that your venture to think of it and after that answer. If you can’t recollect the suitable reaction, it is perfect to tell the examiner that you don’t have the foggiest thought regarding the proper reaction than to give a wrong answer. Act naturally in the midst of the meeting. Make an effort not to endeavour to copy others. You ought to concentrate on your non-verbal correspondence. You ought to have an eye contact with the examiner it will help you to have some assurance. By and by, as you understand what to do before and in the midst of the meeting let us see a segment of the request that you may be asked.
What is UNIX?
This may be the first question that you are asked from the set of unix interview questions. The questions that you are asked may seem to be very basic and that is really what the interviewer wants to ask. They want to gauge the depth of knowledge that you have regarding UNIX. It is better to have the answers prepared for these basic questions so that we do not falter while answering them.
Coming back to the question the answer to this question is that UNIX is an operating system which is portable in nature and can be used for efficient multitasking and used by various functions which are used by many users. As the nature of this operation system is portable it can be efficiently used on various hardware platforms.
What are filters?
This term is frequently used for referring to any program which can take input from various standard input and do some nature of operations upon that input. After the operation is completed it also has the ability to write the result to the standard output. It is also a nature of the program that can be used in-between two different programs.
Tell the syntax that is followed while issuing commands in shells?
The syntax that is followed while issuing commands under the UNIX shell is
Command [-argument] [-argument] [-argument] [file]
So, you can see that you need to be prepared with all sorts of unix interview questions. You may even be handed over a paper where you have to write codes like that above. So, through preparation is required if you really wish to crack the interview and be the one who is selected for the job.
Tell the key features which are there in Korn Shell?
The key features that are there in Korn Shell are:
- history mechanism which has built-in editor which can simulate emacs or vi
- integer arithmetic which is built-in
- capabilities to perform string manipulation
- aliasing of command
- arrays
- control of job
Tell about the common shells and their indicators?
- sh – Bourne shell
- csh – C Shell
- bash – Bourne Again Shell
- tcsh – enhanced C Shell
- zsh – Z Shell
- ksh – Korn Shell
These are the common shells and their indicators.
Explain what you know about Kernel?

This is the UNIX working framework. It is the ace program that controls the PC’s assets, have the power to allocate them to various clients and to various undertakings. In any case, the Kernel doesn’t bargain specifically with a client. Rather, it begins up a different, intuitive program, called a shell, for every client when he/she sign on.
What do you understand by command substitution?
When a command is processed by a shell this is one of the process that is followed. The commands which are written within a backquote are those which are performed by the shell. They will then replace the outputs which are standard of the command and they will be displayed on the line of the command.
You may be looking that the questions asked are basically those which begins with why and how. These are the types of questions that you must be prepared with. The basic objective of the interviewer is to judge whether you know them properly so that you can apply those in practical field.
What are the responsibilities of Shell?
There are various responsibilities which are performed by a Shell. The responsibilities are:
- Execution of program
- Name substitution of variable and file
- Redirection of I/O
- Hookup of pipeline
- Control of environment
- Programming language interpretation
Explain the difference between system call, library function and UNIX command?
Obviously, this answer is known to you. But then also it is good to refresh your memory ones and to organise the answer so that we can speak as the question is asked.
The answer to this question is that:
System Call: It is a part of the programming that is used by Kernel.
Library function: This is not a part of the Kernel but they are accessible to the users who use the system.
UNIX command: These are programs which are stand-alone in nature and it can have both system call and library function integrated in the programming that it uses.
What are most frequently used network commands in UNIX?
The most frequently used network commands in UNIX are:
- telnet – It is the command that is used for logging remotely
- ping – It is an echo request that is used for testing connectivity
- su – The command that is used for switching user
- ftp – This is a file transfer protocol which is used for copying files
- finger – This is the command that is used for gathering information.
What is the difference between cmp command and diff command?
The cmp command is used for matching two files byte by byte and displaying the mismatch that is found. Whereas, diff command is used for showing the changes which have to be undertaken so that two files can be made similar to one another.
How can you determine the path and set it in UNIX?
Every time a command is entered by you a variable which is called PATH will establish the directory where the shell would search for having that command. In some cases, an error message is displayed this happens when the command is not included in the path that is presented to you. It may also be that the command does not exist at all. Manually the path can be set by one using the command “setpath=[directory path]”
Is it conceivable to see data about a procedure while it is being executed?
Each procedure is particularly recognized by a procedure identifier. It is conceivable to view subtle elements and status with respect to a procedure by utilizing the ps command.
Tell what you know about IPC? Explain the various schemes that are available?
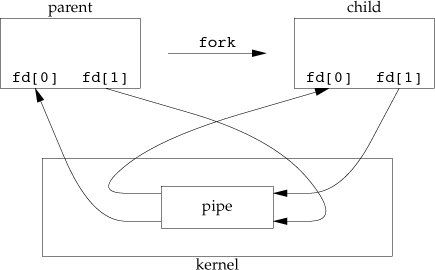
The term IPC (Inter-Process Communication) portrays different routes by which diverse process running on some working framework impart between each other. Different plans accessible are as per the following:
- Pipes: One-way correspondence conspires through which distinctive process can impart. The issue is that the two procedures ought to have a typical precursor (parent-tyke relationship). However this issue was settled with the presentation of named-pipes (FIFO).
- Message Queues: Message Queues can be utilized amongst related and irrelevant procedures running on a machine.
- Shared Memory: This is the speediest of all IPC plans. The memory that is to be shared is mapped into the address space of the procedures (that are sharing). The speed accomplished is ascribed to the way that there is no kernel inclusion. In any case, this plan needs synchronization.
Different types of synchronization are mutexes, condition-variables, read-write locks, record-locks, and semaphores.
Explain the difference that is there between Swapping and Paging?
Swapping: Entire process is moved from the swap gadget to the principle memory for execution. Process measure must be not exactly or equivalent to the accessible primary memory. It is less demanding to usage and overhead to the framework. Swapping frameworks does not deal with the memory all the more with flexibility when contrasted with the paging frameworks.
Paging: Just the required memory pages are moved to primary memory from the swap gadget for execution. Process measure does not make a difference. Gives the idea of the virtual memory.
It gives more prominent adaptability in mapping the virtual address space into the physical memory of the machine. Enables more number of processes to fit in the primary memory all the while. Permits the more prominent process estimate than the accessible physical memory. Request paging frameworks handle the memory all the more flexibly.
So, you can easily see what nature of question you may be asked while seat for these interviews. The unix interview questions may be mixed and the interviewer may not give you enough time to think and answer. If you fumble it will show the lack of knowledge that you have to the interviewer. So, even if you think that these natures of questions are known to you it is better to go through them once so that there will no chance of fumbling while you are asked such. We will be discussing some more questions which will help you to be fully prepared for such interview and be the one who is selected for the job.
State the states that pages may be in after there is page fault?
The states that pages can be after a page fault are:
- They can be on a swap device and not in memory,
- The pages can be on the list of free page that is there in the main memory,
- They can be in a file which is executable
- The pages can be marked “demand zero”
- They can also be marked as “demand fill”.
What is the fault that a page is checked first?
Validity fault is the fault that a page is checked for when it is seen that the page is invalid. The validity fault handler is returned instantaneously and the process incurs the page default validity. The validity fault is taken care by the Kernel and Protection fault is taken care by the process.
What leads to a deadlock when swapping is done to a process?
The conditions which may lead to a deadlock are:
- If it is that all processes that is there in the main memory are asleep.
- All the processes which are ‘ready-to-run’ are swapped out.
- There is less space present in the swap device for adjusting the process which is swapped away from main memory.
- The main memory does not have any space so that it can adjust the new process.
Mention the data structures that are required for Demand Paging?
There are four types of data structure in Kernel for demand paging. They are:
- Page table entries,
- Disk block descriptors,
- Page frame data table (pfdata),
- Swap-use table.
Explain the main goal of having Memory Management?
The main goal of having Memory Management is:
- It is which that decides which process should be included in the main memory.
- This is what which manages the various parts of the virtual address space which is of nature non-core resident.
- It is that which monitors the main memory and it is one which writes the processes periodically to the swap device so that more process can fit into the memory.
What are the system calls that are used by I/O?
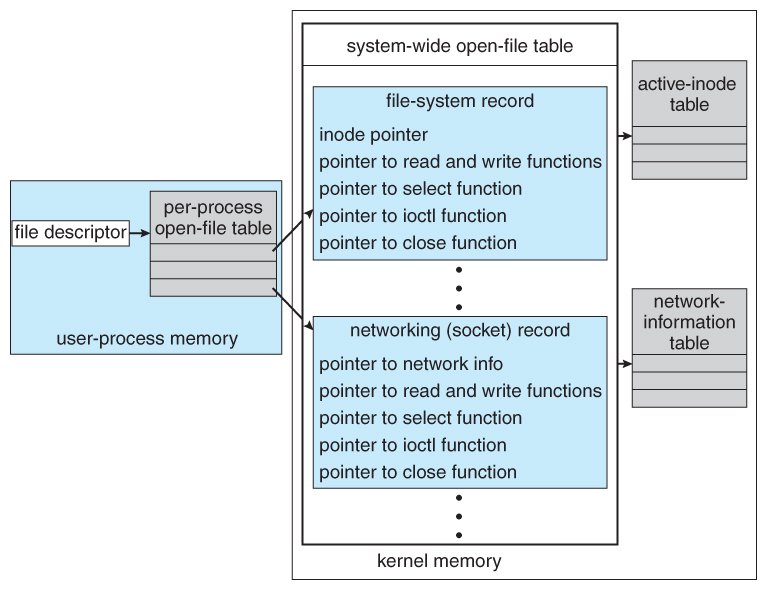
- open(pathname,flag,mode) – open file
- creat(pathname,mode) – create file
- close(filedes) – close an open file
- read(filedes,buffer,bytes) – read data from an open file
- write(filedes,buffer,bytes) – write data to an open file
- lseek(filedes,offset,from) – position an open file
- dup(filedes) – duplicate an existing file descriptor
- dup2(oldfd,newfd) – duplicate to a desired file descriptor
- fcntl(filedes,cmd,arg) – change properties of an open file
- ioctl(filedes,request,arg) – change the behaviour of an open file
Explain how you change the permission for File access?
Every file has following attributes:
- owner’s user ID ( 16 bit integer )
- owner’s group ID ( 16 bit integer )
- File access mode word
‘r w x -r w x- r w x’
(user permission-group permission-others permission)
r-read, w-write, x-execute
chmod is used for changing the mode of access. (filename,mode).
Example 1:
To change mode of myfile to ‘rw-rw-r–‘ (ie. read, write permission for user – read,write permission for group – only read permission for others) we give the args as:
chmod(myfile,0664) .
Each operation is represented by discrete values
‘r’ is 4
‘w’ is 2
‘x’ is 1
Therefore, for ‘rw’ the value is 6(4+2).
Example 2:
To change mode of myfile to ‘rwxr–r–‘ we give the args as:
chmod(myfile,0744).
So, we can now say that these are the questions which are generally asked in an interview on UNIX. It is good that you have this set with you. Start preparing now and do not waste any time. It is good if you go through the questions more than once so that they get imprinted in your mind. I do not suggest memorizing them but reading along a number of times will help you a lot in to be successful in the interview.
It must be said that there is instability related with meetings yet in the event that you can ensure that you finish your work legitimately before going for a meeting you will be able to face that with more confirmation. Never show your uneasiness or disarray to the inspector. They may mix the words in such a course, to the point that reasonable demand may have every one of the reserves of being troublesome. Keep an accumulated identity and consider the question and a while later answer that. It can without a lot of clarification be said that you know all as to UNIX along these lines, you can answer any of the unix interview questions that are heaved at you by the interviewer.





Fqxmyp
22 Feb 2023buy lanoxin 250 mg buy digoxin 250mg without prescription molnupiravir us
Mfwvdl
23 Feb 2023order digoxin lanoxin 250 mg canada buy molnunat without prescription
Scxjjc
24 Feb 2023buy generic acetazolamide 250 mg buy acetazolamide 250 mg online imuran 25mg brand
Migkic
25 Feb 2023diamox 250mg over the counter generic azathioprine 50mg order imuran 50mg online
Zqlmbk
26 Feb 2023buy generic digoxin purchase micardis pills molnunat 200 mg us
Xaydii
27 Feb 2023order generic lanoxin 250 mg order molnupiravir 200mg online molnunat tablet
Tmlmet
28 Feb 2023generic amoxil amoxicillin 250mg generic buy ivermectin canada
Uiundn
28 Feb 2023order amoxil 250mg online stromectol pills ivermectin 3 mg otc
Umtosi
28 Feb 2023coreg oral ditropan 2.5mg brand order amitriptyline 10mg sale
Ymxioz
1 Mar 2023buy carvedilol without prescription order amitriptyline 50mg generic purchase elavil
Czazfb
1 Mar 2023priligy 90mg over the counter buy avana 200mg purchase motilium online cheap
Xrkatq
2 Mar 2023dapoxetine 60mg cheap buy motilium generic domperidone 10mg brand
Selpwm
2 Mar 2023fosamax 35mg price nitrofurantoin 100 mg for sale motrin 400mg uk
Utcdyl
2 Mar 2023alendronate brand brand furadantin brand motrin
Ezozpv
3 Mar 2023indomethacin 50mg over the counter buy cenforce online cenforce 100mg pill
Wontyn
3 Mar 2023indocin 50mg over the counter flomax 0.4mg without prescription cenforce 100mg drug
Dhfguf
3 Mar 2023nortriptyline 25mg pill nortriptyline oral paroxetine 20mg oral
Jhszfn
4 Mar 2023buy nortriptyline 25 mg generic panadol 500mg cheap paroxetine buy online
Hljjwi
4 Mar 2023doxycycline over the counter chloroquine price medrol 16 mg pills
Ovcokz
5 Mar 2023order famotidine 40mg pills purchase tacrolimus generic mirtazapine price
Tcqmxn
5 Mar 2023buy doxycycline 100mg sale aralen 250mg oral buy medrol without prescription
Orykcw
5 Mar 2023pepcid pills buy mirtazapine 30mg without prescription mirtazapine 15mg without prescription
Coandi
6 Mar 2023buy tadalafil 20mg generic cost plavix 75mg buy trimox 500mg pill
Rwkwal
6 Mar 2023order requip 1mg online cheap buy calcitriol 0.25mg generic trandate 100mg usa
Tzzvad
7 Mar 2023order requip pills rocaltrol brand labetalol over the counter
Atxoov
7 Mar 2023buy tadacip 20mg for sale buy amoxicillin buy trimox 500mg online
how to get promo code on 1xbet
7 Mar 2023how to get promo code in 1xbet. Click Here:👉 https://www.lafp.org/includes/pages/1xbet-promo-code-1xbet-bonus.html
Inopvw
8 Mar 2023fenofibrate 160mg without prescription fenofibrate 200mg over the counter purchase viagra generic
видео секс чат рулетка
8 Mar 2023порно чат рулетка видео. Click Here:👉 https://rt.beautygocams.com/
Rgrabf
8 Mar 2023generic nexium 40mg purchase biaxin sale furosemide cost
Uijgid
8 Mar 2023fenofibrate 160mg usa viagra 50mg pill cost viagra
Rspdmq
8 Mar 2023esomeprazole drug order furosemide 40mg for sale lasix 40mg drug
промокод мелбет украина
9 Mar 2023мелбет промокод при регистрации. Click Here:👉 https://mebel-3d.ru/libraries/news/?melbet_2020_promokod_dlya_registracii_besplatno.html
Hohydo
9 Mar 2023buy tadalafil 10mg online Cialis online store order viagra 100mg
Xtvhrp
9 Mar 2023order minocycline pills buy minocin 100mg generic hytrin 1mg price
Rqvztc
10 Mar 2023cialis mail order us Fda approved cialis oral sildenafil
Fumoss
10 Mar 2023minocin 50mg price order minocin capsules terazosin 1mg canada
Itbphs
11 Mar 2023purchase tadalafil Free cialis samples erection pills that work
Ladzlt
11 Mar 2023order glucophage 1000mg pills buy calan online cheap order nolvadex generic
Twgegl
12 Mar 2023buy generic tadalafil 10mg ed pills cheap buy ed medication online
Gzidfx
12 Mar 2023glucophage 500mg ca buy tamoxifen 10mg pills purchase nolvadex without prescription
Sfdcfp
13 Mar 2023provigil 100mg cost provigil online buy promethazine 25mg generic
Ddddyz
13 Mar 2023clomid 50mg price buy prednisolone 20mg online cheap order prednisolone 20mg pills
Suetqh
13 Mar 2023buy provigil 100mg pill oral provigil promethazine pills
Uemlfe
14 Mar 2023clomid over the counter buy prednisolone 10mg pills order prednisolone generic
Ssjjqg
15 Mar 2023prednisone 10mg without prescription brand isotretinoin 10mg order amoxicillin 1000mg
Agmmnz
15 Mar 2023buy accutane 20mg generic order generic ampicillin 250mg purchase ampicillin pill
Ayqjar
15 Mar 2023prednisone 40mg us accutane 20mg drug buy amoxil 250mg online
Weoous
16 Mar 2023order isotretinoin 20mg generic ampicillin cheap purchase ampicillin pills
Zthwgm
17 Mar 2023purchase fildena pill sildenafil 100mg brand propecia 1mg without prescription
Kjuwcv
17 Mar 2023ivermectin virus buy stromectol 12mg sale prednisone order
Wilbek
17 Mar 2023order sildenafil online cheap lyrica 75mg uk finasteride over the counter
code promo 1xbet burkina
17 Mar 2023Code Promo 1xBet https://www.planeterenault.com/UserFiles/files/?code_promo_69.html
Xvuggo
18 Mar 2023ivermectin 3mg pills for humans sexual dysfunction order deltasone for sale
promo code for 1xbet nepal
18 Mar 2023Code Promo 1xBet https://luxe.tv/wp-includes/jki/1xbet-new-registration-promo-code-bangladesh-bonus.html
Jcntol
19 Mar 2023zofran 8mg drug buy sulfamethoxazole online cheap oral bactrim 960mg
비아그라 구매 비아그라 판매
19 Mar 2023Woah! I’m really digging the template/theme
of this blog. It’s simple, yet effective. A lot of
times it’s challenging to get that “perfect balance” between user friendliness and appearance.
I must say that you’ve done a great job with this.
In addition, the blog loads extremely fast for me on Chrome.
Exceptional Blog!
Tluvde
19 Mar 2023order accutane 20mg pills accutane 10mg brand zithromax 250mg cost
Jdroks
19 Mar 2023ondansetron without prescription buy zofran generic brand sulfamethoxazole
Tujlfx
20 Mar 2023accutane order online buy generic azithromycin buy zithromax 500mg for sale
Rlksun
21 Mar 2023purchase ventolin inhalator online cheap augmentin 375mg pill buy amoxiclav sale
Usmbkg
21 Mar 2023ventolin 2mg oral cheap augmentin 375mg buy augmentin 1000mg online
Tlhpqs
22 Mar 2023prednisolone 10mg uk neurontin without prescription buy lasix 100mg sale
Xxhvts
22 Mar 2023prednisolone 10mg over the counter cheap prednisolone without prescription lasix for sale online
Pmkjbt
23 Mar 2023provigil 100mg us buy modafinil online cheap order lopressor 100mg sale
Empgnm
23 Mar 2023order modafinil 200mg without prescription buy generic lopressor buy generic metoprolol 50mg
Edserq
24 Mar 2023doxycycline usa vibra-tabs medication zovirax online order
Qauhex
25 Mar 2023avodart pill dutasteride cost xenical 60mg usa
Nltyrc
25 Mar 2023order doxycycline 100mg brand vardenafil acyclovir 400mg usa
Ixtwiv
25 Mar 2023dutasteride usa cost cephalexin 500mg xenical 120mg over the counter
Dhciyx
27 Mar 2023oxybutynin 5mg over the counter oxybutynin 5mg ca buy trileptal 600mg pills
Zhwrtr
27 Mar 2023azathioprine us buy imuran 25mg online naproxen 250mg pills
Qhtcoh
28 Mar 2023oxybutynin usa oxybutynin 2.5mg drug order trileptal online
Wkoiim
28 Mar 2023buy cefdinir 300mg sale order omnicef generic protonix usa
Zeojdl
29 Mar 2023order zocor 10mg buy promethazine online cheap sildenafil professional
Kajgff
29 Mar 2023omnicef 300 mg ca buy lansoprazole generic pantoprazole 40mg over the counter
Umsxod
29 Mar 2023zocor 10mg generic zocor 10mg drug sildenafil drug
Ioarhe
30 Mar 2023dapsone without prescription dapsone 100mg usa buy tenormin without prescription
Vykktf
31 Mar 2023dapsone for sale online avlosulfon 100 mg us generic tenormin
Szuiec
31 Mar 2023cost uroxatral 10mg buy uroxatral 10 mg for sale diltiazem ca
Bxupai
31 Mar 2023order alfuzosin generic uroxatral generic buy diltiazem 180mg generic
Vgzhxr
1 Apr 2023usa viagra overnight viagra mail order usa tadalafil 40mg uk
Checking wallets
1 Apr 2023ZkSync Free Airdrop Crypto: Your Guide to Free Coins in 2023, EARN MORE THAN $1000! https://youtu.be/o1JvjQA-s-M
Yygtsp
2 Apr 2023oral viagra viagra fast shipping real cialis pills
Hxpcgh
2 Apr 2023buy ezetimibe 10mg purchase sumycin without prescription methotrexate 5mg uk
Zlsswf
3 Apr 2023order ezetimibe 10mg for sale buy ezetimibe sale order generic methotrexate 5mg
Pgduea
3 Apr 2023phenergan tablet buy modafinil 100mg online buy tadalafil 5mg online cheap
Mjknim
3 Apr 2023purchase promethazine generic promethazine order cialis 40mg oral
best world news
4 Apr 2023Yes! Finally something about sepornews.
Koreysuito
4 Apr 2023Wow Look At Amazin News Website Daily Worldwide [url=https://sepornews.xyz]Sepor News[/url]
canada drug store
4 Apr 2023price drugs
Jvxhik
4 Apr 2023coumadin 2mg over the counter purchase metoclopramide for sale oral zyloprim 300mg
Dpsent
5 Apr 2023buy levofloxacin 250mg pills order levaquin 250mg without prescription zyban 150 mg cost
Cglxna
5 Apr 2023warfarin 5mg sale reglan 20mg price zyloprim 300mg cost
Tzrevb
5 Apr 2023buy levofloxacin pills buy levaquin cheap zyban ca
canada drugs without perscription
6 Apr 2023canada online pharmacy
canadian pharmacies recommended by aarp
6 Apr 2023online canadian pharmaceutical companies
Rlvelx
6 Apr 2023order cetirizine 10mg for sale buy strattera 25mg pill zoloft medication
Jdnceb
6 Apr 2023buy cenforce pill cenforce 100mg tablet glycomet cheap
Nwajwh
8 Apr 2023zyrtec uk buy cetirizine 5mg buy sertraline online
Kgkbwv
8 Apr 2023escitalopram sale revia 50mg ca order naltrexone 50mg online cheap
Widget Blogger
8 Apr 2023Hi to all, how is everything, I think every one is getting more from this website,
and your views are fastidious designed for new users.
Utedur
8 Apr 2023cenforce drug chloroquine for sale online glycomet 1000mg canada
Umnrij
8 Apr 2023buy atorvastatin 20mg generic cheap viagra without prescription cheap sildenafil pills
canadian online pharmacies legitimate by aarp
9 Apr 2023prescription drugs without doctor approval
Ergazk
9 Apr 2023generic escitalopram revia medication oral naltrexone 50mg
the best canadian online pharmacy
9 Apr 2023best rated canadian pharmacies
Jfcsdm
9 Apr 2023purchase femara pills femara cost buy viagra 100mg online
Nsxzkg
10 Apr 2023lipitor 20mg sale buy viagra 50mg without prescription sildenafil professional
Vzwipp
10 Apr 2023canadian cialis and healthcare cialis buy buy generic ed pills for sale
Pznonr
10 Apr 2023letrozole 2.5 mg us cost sildenafil buy viagra tablets
Mnonih
10 Apr 2023buy cialis 5mg without prescription real cialis online buy ed pills cheap
Sybnjx
12 Apr 2023order cialis online usa pharmacy cialis buy cheap ed pills
Kkzumm
12 Apr 2023ivermectin 3mg tabs buy prednisone 5mg generic accutane cheap
Ccvvcy
12 Apr 2023brand tadalafil 40mg buy no rx tadalafil otc ed pills
Ugazms
12 Apr 2023modafinil 100mg us prednisone 10mg price cheap deltasone 20mg
best mexican pharmacy
12 Apr 2023list of legitimate canadian pharmacies
order prescription medicine online without prescription
13 Apr 2023canada mail pharmacy
Qsbwdp
13 Apr 2023ivermectin 3 mg for humans stromectol 6mg us order accutane for sale
Xnwbko
13 Apr 2023amoxicillin 1000mg canada buy amoxil 500mg pill buy prednisolone
Oahqpj
14 Apr 2023buy generic modafinil over the counter provigil us deltasone 10mg usa
Txnscq
14 Apr 2023purchase accutane generic accutane 20mg drug azithromycin online order
Uzgzeg
14 Apr 2023order amoxicillin pill amoxil ca prednisolone 5mg for sale
Bpgogb
15 Apr 2023buy gabapentin 600mg order generic neurontin buy doxycycline 100mg sale
my mexican pharmacy
15 Apr 2023canadian pharmaceutical prices
Oqwntx
16 Apr 2023accutane 10mg brand azithromycin 250mg over the counter azithromycin 250mg without prescription
Qrgovy
16 Apr 2023prednisolone 20mg for sale gabapentin 600mg cost buy furosemide 100mg pills
Unmeuy
16 Apr 2023gabapentin uk purchase monodox pills doxycycline over the counter
Kitxeg
16 Apr 2023albuterol ca purchase amoxiclav pill cheap levoxyl pills
Slesta
17 Apr 2023albuterol cheap purchase amoxiclav online cheap synthroid 100mcg pill
Mgpaoz
17 Apr 2023order clomiphene 100mg pill plaquenil 400mg usa hydroxychloroquine usa
mail order pharmacies
17 Apr 2023most reliable canadian pharmacies
discount prescription drug
17 Apr 2023no prescription pharmacies
prescriptions canada
18 Apr 2023legit canadian online pharmacy
medication online
18 Apr 2023drugs online
Vkiqsj
18 Apr 2023buy prednisolone 10mg online buy prednisolone 5mg pill furosemide 40mg oral
Iuzomj
18 Apr 2023monodox over the counter order ventolin 2mg generic purchase amoxiclav generic
Iknbtp
18 Apr 2023order clomiphene 50mg online cheap buy generic hydroxychloroquine for sale order hydroxychloroquine 400mg generic
Eperfx
19 Apr 2023order tenormin 100mg without prescription atenolol 50mg cost letrozole 2.5 mg without prescription
pharmacies with no prescription
19 Apr 2023canadain pharmacy no prescription
buy prescription drugs online
19 Apr 2023pharmacy canadian
Zbhcdk
20 Apr 2023doxycycline 100mg price purchase ventolin inhalator generic buy clavulanate medication
Ewbygj
20 Apr 2023synthroid usa buy levothyroxine no prescription order generic vardenafil
Wabqaw
20 Apr 2023buy tenormin 50mg sale methylprednisolone 4mg over counter letrozole for sale online
Zukrmu
20 Apr 2023albendazole buy online order aripiprazole 20mg without prescription buy provera for sale
no prescription pharmacy
20 Apr 2023legitimate online pharmacy
Jtlgbp
21 Apr 2023levothyroxine pills buy vardenafil 20mg online buy vardenafil 20mg generic
Uyagws
21 Apr 2023buy generic glucophage order norvasc 5mg pills order amlodipine generic
Ffksuj
21 Apr 2023buy generic albenza 400mg buy generic abilify 20mg provera usa
Pyzcjv
22 Apr 2023glycomet canada buy glycomet sale brand amlodipine
Jejmxv
22 Apr 2023zestril 10mg over the counter purchase lopressor generic metoprolol cost
Ccrwxn
22 Apr 2023order biltricide 600 mg online purchase praziquantel online cheap buy cyproheptadine 4mg
Hibnxs
22 Apr 2023order lyrica pill order claritin 10mg pills priligy without prescription
Gbzpro
23 Apr 2023lisinopril 10mg price buy lisinopril 10mg order metoprolol 50mg online
Hbgmul
23 Apr 2023methotrexate order purchase reglan pills oral metoclopramide 20mg
Uatubf
24 Apr 2023order pregabalin pills buy lyrica 75mg without prescription priligy price
Jqaahm
24 Apr 2023xenical 60mg pill orlistat 120mg uk zyloprim cost
levitra from canadian pharmacy
24 Apr 202324 hour pharmacy
Caugyf
25 Apr 2023methotrexate 5mg canada metoclopramide medication buy metoclopramide generic
Ssmvkz
25 Apr 2023losartan pills buy losartan paypal topamax over the counter
Lqrpjl
25 Apr 2023buy orlistat 60mg sale purchase allopurinol online order allopurinol 100mg online cheap
Ewzljf
25 Apr 2023brand rosuvastatin cost rosuvastatin purchase domperidone without prescription
Zydepa
26 Apr 2023buy generic cozaar 50mg order hyzaar pills buy topiramate paypal
Lwmpmp
26 Apr 2023sumatriptan 25mg usa levofloxacin generic cheap avodart
Bwjeta
26 Apr 2023rosuvastatin cheap order zetia pills generic motilium 10mg
Aendcs
26 Apr 2023sumycin 500mg uk order baclofen 10mg pill buy ozobax pills for sale
Hrtfgg
28 Apr 2023buy sumatriptan 25mg pills purchase imitrex sale dutasteride buy online
Lihjcy
28 Apr 2023buy sumycin 500mg generic buy cheap generic baclofen order baclofen 10mg generic
Lymtdy
28 Apr 2023toradol online buy buy propranolol buy inderal 10mg pill
Hlvphh
28 Apr 2023zantac 150mg ca buy ranitidine 300mg for sale purchase celecoxib pill
Derbe Hamburg
28 Apr 2023Hey there, I think your site might be having browser compatibility issues.
When I look at your website in Opera, it looks fine but when opening in Internet Explorer,
it has some overlapping. I just wanted to give you a quick
heads up! Other then that, very good blog!
Ikcuof
29 Apr 2023buy ketorolac tablets buy toradol online cheap inderal 10mg drug
Yfpkgz
29 Apr 2023clopidogrel uk clopidogrel 75mg pill buy nizoral 200mg pill
Oxfotn
29 Apr 2023cheap zantac 150mg ranitidine 300mg cost buy generic celecoxib online
Pbyefh
29 Apr 2023flomax us order flomax 0.4mg pill buy spironolactone 25mg without prescription
Uvmmhp
30 Apr 2023purchase clopidogrel buy clopidogrel 150mg online buy generic nizoral over the counter
Mulura
30 Apr 2023cymbalta 40mg uk order piracetam 800 mg order nootropil 800mg online
Fohwny
1 May 2023tamsulosin canada buy ondansetron online buy generic spironolactone
Lpjgfe
1 May 2023betnovate 20gm ca sporanox 100 mg uk sporanox 100 mg brand
Fqkgyb
2 May 2023order cymbalta online order cymbalta 20mg pill piracetam 800mg uk
Udsgtt
2 May 2023purchase combivent pill decadron 0,5 mg without prescription how to get zyvox without a prescription
Ulpqdx
2 May 2023betamethasone 20gm cost betamethasone drug sporanox 100mg over the counter
Dtoeim
2 May 2023buy progesterone without a prescription brand tinidazole 500mg purchase zyprexa online
overseas pharmacy
3 May 2023buy canadian drugs online
Jxrkrv
3 May 2023combivent medication buy linezolid 600 mg buy generic zyvox over the counter
Ngober
3 May 2023order nateglinide for sale order candesartan candesartan drug
Jqghod
4 May 2023prometrium 100mg usa buy zyprexa no prescription order zyprexa 10mg
Gtlwhp
4 May 2023bystolic pill order clozaril 50mg sale purchase clozapine generic
Awaeqq
5 May 2023order bystolic 5mg generic cost clozaril 100mg clozaril 100mg oral
Qqonzk
5 May 2023simvastatin us sildenafil on line oral viagra 50mg
Yyulqs
5 May 2023starlix 120 mg usa cost capoten candesartan cost
Gnvjpi
6 May 2023carbamazepine 400mg pills ciplox 500mg for sale generic lincocin 500mg
^Inregistrare pe www.binance.com
6 May 2023Thanks for sharing. I read many of your blog posts, cool, your blog is very good. https://www.binance.com/ro/register?ref=V3MG69RO
Ntfcai
6 May 2023zocor 20mg pill buy sildenafil 100mg oral viagra 50mg
canada drugs
7 May 2023canadian internet pharmacies
canadian drugs without any prescriptions
7 May 2023medicine from canada with no prescriptions
Xcyprn
7 May 2023cialis 10mg for sale cialis use sildenafil 50mg pills
Pacwad
8 May 2023order tegretol 400mg pill ciprofloxacin 500mg price lincocin 500 mg generic
izveidot binance kontu
8 May 2023Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me? https://www.binance.com/lv/register?ref=53551167
Mgmhmh
9 May 2023buy tadalafil 40mg generic how to get cialis buy sildenafil 100mg pills
Coluxo
9 May 2023buy cefadroxil 250mg online cheap where can i buy epivir oral proscar
Dgkuxv
9 May 2023buy cefadroxil 250mg online finasteride 1mg canada finasteride medication
Qeeqpx
9 May 2023estradiol 2mg us cheap estrace 1mg buy generic minipress for sale
binance Konta Izveidosana
10 May 2023I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://www.binance.com/lv/register?ref=IJFGOAID
Mdbrjk
10 May 2023diflucan 200mg cost diflucan sale order ciprofloxacin 1000mg generic
Zrbwdb
10 May 2023generic estrace 2mg prazosin ca order prazosin for sale
Zvkjrw
10 May 2023diflucan 200mg oral ampicillin 250mg ca cipro 500mg brand
Ckwqfz
11 May 2023buy vermox 100mg order tretinoin gel without prescription order tadalis 10mg without prescription
assiste
11 May 2023Loxoprofen Loxoprofene where to buy cialis online
Pbuvgq
12 May 2023buy cheap generic metronidazole cephalexin uk cephalexin us
Ppiyoi
12 May 2023generic mebendazole 100mg order tretinoin cream without prescription cost tadalafil
Bysibo
12 May 2023buy flagyl 200mg pill buy metronidazole 200mg sale purchase keflex sale
Knitwp
12 May 2023brand avanafil tadalafil 10mg cost voltaren for sale
creek gate io
12 May 2023At the beginning, I was still puzzled. Since I read your article, I have been very impressed. It has provided a lot of innovative ideas for my thesis related to gate.io. Thank u. But I still have some doubts, can you help me? Thanks.
Chlphi
13 May 2023buy cleocin pills buy cleocin no prescription purchase sildenafil generic
Vrhuvl
13 May 2023order avanafil 100mg pill avanafil 200mg canada voltaren 100mg without prescription
Oqxsar
13 May 2023order cleocin for sale buy clindamycin pill buy ed medications
Ylwvkc
14 May 2023indocin 75mg ca buy indomethacin 50mg online order cefixime 200mg generic
Qospma
15 May 2023buy indomethacin paypal cefixime for sale buy suprax
Mhatgj
15 May 2023buy nolvadex 20mg ceftin price ceftin pills
Ulumry
15 May 2023where can i buy tamoxifen order nolvadex pill buy cefuroxime without a prescription
Xeszaz
15 May 2023buy trimox pills anastrozole 1 mg sale clarithromycin over the counter
binance Sign Up
16 May 2023Your article helped me a lot, is there any more related content? Thanks!
Bnhrup
16 May 2023purchase trimox sale order clarithromycin buy biaxin 250mg without prescription